Identity And Access Management
Personality and Access The executives is a principal and basic network protection ability. Basically, with its attention on fundamental and applied exploration and principles, NIST tries to guarantee the perfect individuals and things have the right admittance to the ideal assets at the ideal time.
Conducts centered examination to all the more likely see new and arising innovations, their effect on existing guidelines, and the execution of character and access the executives arrangements;
Leads in the improvement of public and worldwide personality and access the executives principles, direction, best practices, profiles, and systems to make an upgraded, interoperable set-up of secure, protection improving arrangements, including confirmation and approval inside the Web of Things (IoT);
Develops its personality and access the board principles, rules and assets; and
Produces model arrangements that unite the character the board and network safety necessities expected to address explicit business online protection challenges.
Through this Personality and Access The board Asset Center, we look to share our endeavors that reinforce the security, protection, ease of use and interoperability of arrangements that meet an association's character and access the executives needs all through the framework lifecycle.
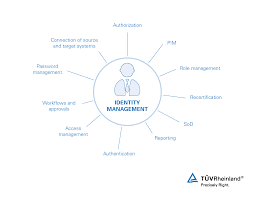
Character and access the board (IAM) is a structure of business cycles, arrangements and advancements that works with the administration of electronic or computerized personalities. With an IAM system set up, data innovation (IT) supervisors can handle client admittance to basic data inside their associations. Frameworks utilized for IAM remember single sign for frameworks, two-factor validation, multifaceted verification and restricted admittance the board. These advances likewise give the capacity to safely store personality and profile information just as information administration capacities to guarantee that main information that is vital and pertinent is shared.
IAM frameworks can be conveyed on premises, given by an outsider seller through a cloud-based membership model or sent in a half and half model.
how people are recognized in a framework (comprehend the distinction between character the board and validation);
how jobs are distinguished in a framework and how they are doled out to people;
adding, eliminating and refreshing people and their parts in a framework; legating levels of admittance to people or gatherings of people; and ensuring the delicate information inside the framework and getting the actual framework.
Organizations pioneers and IT divisions are under expanded administrative and authoritative strain to secure admittance to corporate assets. Accordingly, they can presently don't depend on manual and mistake inclined cycles to allocate and follow client advantages. IAM mechanizes these assignments and empowers granular access control and examining of all corporate resources on premises and in the cloud.
IAM, which has a steadily expanding rundown of elements - - including biometrics, conduct examination and computer based intelligence - - is appropriate to the afflictions of the new security scene. For instance, IAM's tight control of asset access in profoundly dispersed and dynamic conditions lines up with the business' progress from firewalls to zero-trust models and with the security necessities of IoT. For more data on the eventual fate of IoT security, look at this video.
Comments
Post a Comment